Active Directory Auditing: Finding the Source of Locked Accounts in AD
Without the right tools Active Directory Auditing can be an extremely painful task not dissimilar to finding a needle in a haystack. Today we’ll take a look at troubleshooting repeated user account lockouts in Active Directory and try to determine from which computer or device the lock is originating.
Firstly, it is important to note that there may be several domain controllers within the production environment with some level of replication occurring between them. What this means is if NT user Bob’s initial lockout occurs on DC#1 (Domain Controller #1) this status will be automatically replicated to all the other DC’s. However, if using Active Directory you’ll probably miss all this as more than likely it’s only showing the status according to a single DC it’s connected to. Another important thing to note is that lockouts can occur from a range of events including:
- Stored user names and passwords contain redundant credentials
- Brute-force attack (check whether RDP port 3389 is open to the internet)
- Active Directory replication
- Programs with cached user credentials
- Service accounts with recently changed or expired passwords
- Low password threshold (set too low)
- User logging on to multiple computers
- Scheduled tasks that utilizes user instead of service accounts
- Shared drive mappings
- Disconnected Terminal Server sessions
- Mobile devices accessing exchange server
Finding the culprit
– source from which the account was locked
If you have the time and feel lucky, logon to the DC and launch the Computer Management tool. Proceed to System Tools > Event Viewer > Windows Log > Security and start sivving 🙂
Otherwise, go on over to Microsoft.com and grab a copy of a nifty tool-set they call Account Lockout and Management Tools, this should save you some time.
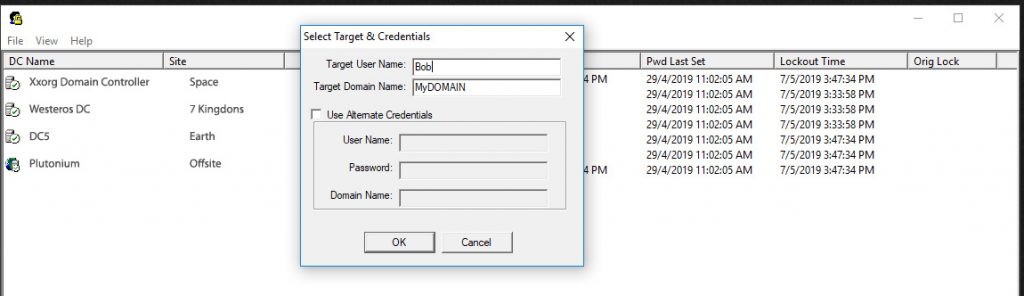
After downloading, extract the contents to a folder and run the standalone LockoutStatus.exe file. An interface similar to above should appear. Goto File, Select Target and insert the username in question as well as the name for any of your domain controllers. Once that is done you should get a visual of the account’s status on ALL domain controllers. Other columns include Bad Password Count, timestamps and Orig Lock corresponding to when exactly each status was set.
Join the Newsletter
Sign up for our personalized daily newsletter




